These Are the Most Common Passwords—Do Yours Make the List?

If your password appears on this passwords list, you're an easy target for hackers.
When it comes to creating an online account, many of us would rather remember a code than create really good passwords. In our defense, it’s hard to keep track of endless log-ins! According to technology expert Burton Kelso, it’s human nature to fall into a predictable routine when it comes to our passwords list. “We tend to create passwords based on things familiar to us, such as common words, names, and locations,” he explains.
That’s not the only password sin we’re guilty of. “It’s tempting to use one easy-to-remember password, like your dog’s name, for all your passwords. These kinds of passwords make people feel safe because they’re so easy to remember,” says George Finney, the chief information security officer at Southern Methodist University. “Today, it’s about as difficult for a cybercriminal to get your password as it is to make a cup of coffee, particularly if you use the same passwords for everything you do online.”
But as they say, knowledge is power. To stay safe online and avoid spyware, identity theft, and other issues, you need to know a few secrets that hackers don’t want you to know—including the fact that they’ll first try these common methods and use a passwords list in order to get their hands on your personal information. Start by making sure your passwords don’t appear below. If they do, replace them with strong passwords and boost your online security by using two-factor authentication. Then learn how to tell if your computer has been hacked so you can tackle a breach as soon as it occurs.
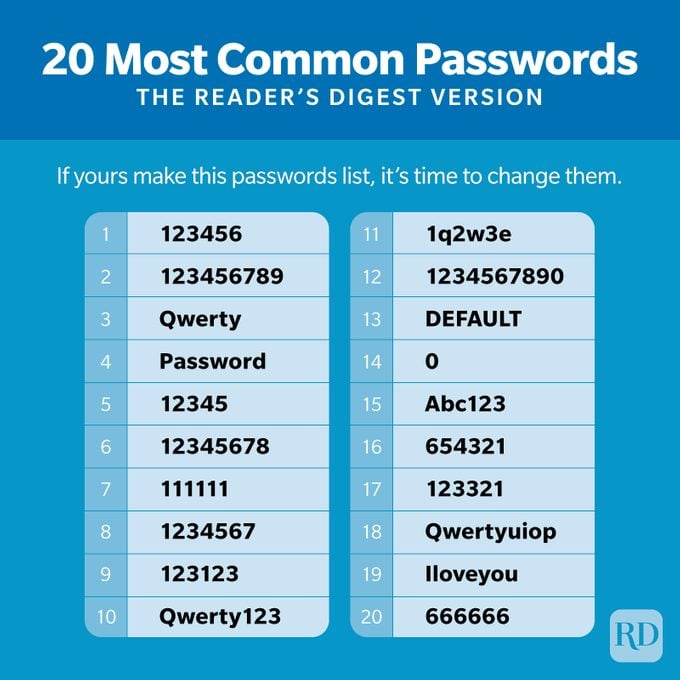
The top 20 most common passwords list
Mobile security firm Lookout recently published a passwords list of the 20 most common passwords found in leaked account information on the dark web. Some of the most commonly used passwords are obvious, but others are a bit more surprising.
- 123456
- 123456789
- Qwerty
- Password
- 12345
- 12345678
- 111111
- 1234567
- 123123
- Qwerty123
- 1q2w3e
- 1234567890
- DEFAULT
- 0
- Abc123
- 654321
- 123321
- Qwertyuiop
- Iloveyou
- 666666
How hackers use a passwords list
There are several websites that offer password lists, says Kelso. While the intention of most of them is to encourage people to shy away from the most common passwords, they can inadvertently give hackers a leg up. Mark Burnett, a security consultant and researcher, recently published 10 million passwords on his website, Xato.net, to provide a better understanding of how people formulate passwords. It’s useful information, but it also gives hackers a really good place to start.
Consider the alarming things a hacker can do with just your email address: With no information beyond that, they can use “password spraying” to test passwords on these lists to see if any work with your email address. “Often hackers use bots to run these tests, and only if a match is found does a hacker then use the valid credentials to try taking over the account,” says Hari Ravichandran, CEO of digital security company Aura.
Avoid picking from a passwords list, and you won’t fall prey to this type of hacking. That’ll come in handy if hackers have your cell phone number as well.
Beyond the passwords list
A list of passwords is just the starting point for hackers. Bad actors use plenty of other tactics to figure out your passwords.
They try sequential number combinations
As you can see from the passwords list above, the majority of passwords have one thing in common: sequential numbers, like 12345. Avoid these at all costs, say security experts. They’re also a no-no when it comes to the four-digit PIN you use with your debit card. In case you need a new one, here is the world’s safest PIN.
They guess common phrases
Avoid using common words or phrases. Yep, they’re easy to recall, but they’ll also be among the first passwords that hackers will guess. On a list of the most common passwords, the word “password” makes the top five, the phrase “iloveyou” makes the top 20, and the words “sunshine,” “princess,” and “dragon” are incredibly popular.
Hackers will also try common words with case and numerical substitutions, according to Kelso. So they won’t just test October—they’ll try october and 0ct0ber too.
They try pet and family names
According to Google, you should never, ever include your pet’s, child’s, or spouse’s name in your password. A hacker who’s privy to any of your personal information will definitely check your loved ones’ monikers to try to break your code. “If a hacker has access to any of your personal information, they will try that information to gain access,” says Ravichandran.
They use significant dates
Your birthday, anniversary, or the birthday of a loved one can seem like an obvious password choice to you. After all, you will never forget it. But because it makes sense to you, hackers will also be able to figure it out—and pretty easily—if they have access to your personal information, according to Google.
They turn to the dark web
Sometimes your old passwords can leak onto the dark web, that part of the Internet not visible to search engines. And oftentimes that is where hackers access them. “Hackers often have a toolkit that includes software programs and access to databases that contain lists of emails and often password lists,” says Ravichandran. “When a company experiences a large data breach, those records are often compiled into large databases that are readily available for hackers.”
Data breaches are showing no sign of slowing down, he adds, citing a 2021 report from the Identity Theft Resource Center that found the number of reported data breaches rose 68 percent from 2020. Indeed, leaked data remains one of the top mobile security threats of 2022.
They create bots
If they have exhausted their resources, hackers have one final tool to break your code. They can create a bot that will try every possible combination. “Keep in mind,” says Kelso, “modern computers can make password guesses from 10,000 to more than a billion guesses per second.” That’s enough to make you want to disappear from the Internet for good!
They go phishing
According to Finney, the easiest way for hackers to get your password is to trick you into giving it to them. They fool you through what’s known as a phishing scam, sending out fraudulent emails disguised as the real deal.
“If you do click on a phish, it will usually take you to a fake website that won’t have your password saved,” says Finney, who is also the founder and CEO of Well Aware Security and author of Well Aware: Master the Nine Cybersecurity Habits to Protect Your Future. “Remember, if your password isn’t saved there, don’t type it in!”
They use password reset questions
Have you ever gotten an email asking if you requested a password change, and you didn’t? It was probably a hacker. “Cybercriminals don’t even have to know your password to get into your accounts. They can use your password reset questions to change your password and lock you out of your account,” Finney states.
Say, for instance, you suddenly can’t access your go-to social media apps. You may have been hacked on Instagram or Facebook.
One way to prevent this is to create nonsense answers to security questions, he says. Don’t go for accuracy; pick responses only you would know the answer to. So next time your account asks what your mother’s maiden name is, you might say Luke Skywalker.
How to find out if a hacker has your password
By now, you’re probably wondering if the bad guys have tried those strategies on you—and succeeded. Thankfully, it’s pretty easy to find out whether hackers have your passwords. “Today, thousands of companies have experienced a data breach. Many cybercriminals will post the data they steal to prove that they stole it,” says Finney.
Several organizations, like Have I Been Pwned and some identity-protection services, also gather this information and can help you find out whether cybercriminals have accessed your data. “Usually, you just need to provide an email address to see if you were impacted,” he says, adding that some password managers, like 1Password, will alert you if your log-ins were exposed in a data breach.
If the idea of shady individuals having your data makes you uncomfortable, you’re not alone. Arm yourself with an understanding of other ways your personal information is collected, including through data brokers and cookies, and how it can be used for harmful practices like doxxing.
How to pick a strong password
When it comes to picking a strong password, there are two general criteria to meet: complexity and uniqueness. The more complex, the better. And of course, you don’t want to use the same password twice. Sure, that’ll make it hard to remember your passwords, but it’s a worthy trade-off. In fact, most cybersecurity experts don’t know any of their passwords off the top of their heads.
“I use a password vault like Apple’s Keychain, Dashlane, 1Password, or LastPass,” reveals Finney. “These can help you generate a random, unique password for every website you visit. And they integrate with all your devices and web browsers to do all the remembering for you.”
But if you don’t want to download a security app like a password manager, you have other options. You can store passwords in your browser, for instance. And yes, it’s safe to store passwords in Google Chrome, Finney says. It can even alert you when your username or password has been compromised.
If you store your passwords in Google Chrome, you can see them by opening Chrome and clicking on your profile picture at the top right of your screen. Click the key icon on the pop-up screen to visit a page with all your saved passwords. To view one, click the eye icon. If you lock your computer, you’ll need to first enter your password. That’s a good thing, and if you do allow your browser to store passwords, you should always lock your device with a password.
Finney also recommends enabling two-factor authentication for every account. “Two-factor authentication can be a text message [less secure] or an application like Google Authenticator [more secure],” he says. “You receive a code that validates you are really the person trying to get into the site.”
Once you know what makes for an easy-to-crack passwords list—and how to create stronger passwords—it’s time to beef up the rest of your online privacy and security. For starters, Google is tracking you online, so learn how to browse the Internet anonymously. Then find out how to remove spyware from your iPhone—it may come in handy in the future.
Sources:
- Burton Kelso, technology expert
- George Finney, chief information security officer at Southern Methodist University, founder and CEO of Well Aware Security, and author of Well Aware: Master the Nine Cybersecurity Habits to Protect Your Future
- Hari Ravichandran, CEO of Aura
- Identity Theft Resource Center: “Identity Theft Resource Center’s 2021 Annual Data Breach Report Sets New Record for Number of Compromises”
- Xato: “Today I Am Releasing Ten Million Passwords”